Top Cybersecurity Threats in 2025
Digital Reality Check: Why 2025 Is a Turning Point
The internet used to feel like a tool. In 2025, it feels more like an ecosystem and ecosystems attract predators. Cybersecurity is no longer about protecting machines; it’s about protecting digital life itself.
Banking, healthcare, work, and even personal identity now exist online. When attackers strike, the damage isn’t limited to files it spills into real life.

Top Cybersecurity Threats in 2025
Here you can see the threats of cyber security on the official web for more information.
How Cybercrime Has Quietly Changed
From Noise to Stealth
Earlier cyberattacks were loud. Systems crashed. Screens flashed warnings. Today’s attacks are silent. They observe first, act later, and leave minimal traces.
Crime as a Digital Industry
Cybercrime now operates like a startup culture:
-
Developers build attack tools
-
Marketers sell stolen data
-
Operators execute campaigns
Efficiency has replaced chaos.
The Most Dangerous Cyber Threats of 2025
Self-Learning Attacks
Some attacks now adjust their behavior automatically. If blocked once, they return with a modified strategy.
These threats don’t repeat mistakes.
Data Locking and Digital Extortion
Attackers no longer just encrypt files. They steal them first. Victims are pressured with public exposure, legal trouble, or reputation loss.

Top Cybersecurity Threats in 2025
Hyper-Personalized Scam Messages
Scams now reference real conversations, recent purchases, or workplace hierarchies.
When lies sound familiar, people stop questioning them.
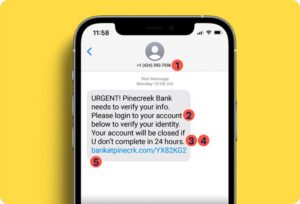
5 Signs that text is SCAM
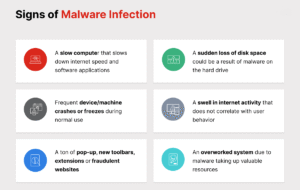
Hidden Threats Inside Trusted Software
Updates, plugins, and third-party tools are abused to distribute malicious code.
Trust becomes the weakness.
Top Cybersecurity Threats in 2025
Cloud Permission Abuse
Attackers often log in instead of breaking in. Over-privileged accounts give them everything they need.
Top Cybersecurity Threats in 2025
Smart Devices as Silent Gateways
Smart devices rarely scream when compromised. They whisper. And while they whisper, they leak data continuously.
Invisible Software Weak Points
Some flaws exist only under rare conditions. Attackers actively hunt these edge cases.
Internal Security Blind Spots
Employees, contractors, and temporary staff often have more access than necessary.
Convenience quietly defeats security.
Identity Hijacking in the Digital Age
Identity theft now includes behavior patterns, login habits, and biometric traits.
Once copied, identity is hard to reclaim.

Right here you will see that how cyber securuty works for real…
Why Traditional Security Is Failing
Static defenses protect against yesterday’s attacks.
Modern threats evolve hourly.
Security that doesn’t learn is already outdated.
How to Defend Yourself in 2025
Identity-Centric Security
Who is requesting access matters more than what device they use.
Behavior-Based Monitoring
Unusual behavior is flagged even if credentials are correct.
Breaking the Trust Assumption
Every request must earn access. Nothing is assumed safe.
Security Hygiene That Actually Works
-
Minimal permissions
-
Regular access reviews
-
Strong authentication
Small habits create strong defenses.
Training the Human Layer
People aren’t the weakest link they’re the most undertrained one.
Personal-Level Cyber Defense
-
Treat links with suspicion
-
Separate work and personal accounts
-
Lock down social media visibility
-
Use device-level encryption
Your digital shadow should be small.
Business-Level Cyber Defense
-
Monitor access continuously
-
Audit third-party tools
-
Secure backups offline
-
Simulate attack scenarios
Preparedness reduces panic.
Threats and Their Most Effective Counters
| Threat Pattern | Best Defensive Response |
|---|---|
| Adaptive malware | Behavior analysis |
| Digital extortion | Isolated backups |
| Targeted scams | Verification policies |
| Supply chain risks | Dependency audits |
| Cloud misuse | Least-privilege access |
| IoT exploitation | Network separation |
| Unknown flaws | Continuous monitoring |
| Insider misuse | Activity logging |
Cybersecurity Tools That Will Matter Next
-
Passwordless login systems
-
Adaptive access engines
-
Security automation platforms
-
Post-quantum encryption
Security is becoming self-aware.
Law, Accountability, and Digital Responsibility
Governments are tightening regulations. Ignoring security now carries financial and legal consequences.
Negligence is no longer defensible.
Life After 2025: Where Security Is Headed
Security will shift from reaction to anticipation. Systems will block threats before damage begins.
The goal is simple: make attacks unprofitable.
CONCLUSION
Cybersecurity in 2025 is not about fear— t’s about foresight. The threats are real, but so are the tools to stop them. Those who adapt will stay protected. Those who delay will pay the price.
Security isn’t paranoia. It’s preparation.
FAQs
1. Why do modern cyberattacks avoid detection?
Because stealth is more profitable than disruption.
2. Are personal users really targeted?
Yes. Individuals are often easier and more valuable targets.
3. Is cloud computing unsafe?
No—but poor access control makes it risky.
4. What matters more: tools or training?
Training. Tools fail without informed users.
5. Can cyber threats ever be eliminated?
No—but they can be made ineffective.
Please don’t forget to leave a review, share if you noticed any threats around your surrounding…






















Recent Comments